Case Study: Phishing Attack Creates Public Links to Private Files
Scenario
An email Phishing attack resulted in unauthorized access to the victim’s email mailbox and the creation of public-sharing links to private Microsoft OneDrive files.
Background
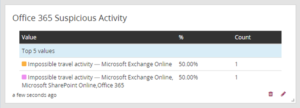
In early 2019, an AIS Managed SIEM Alert indicated that a Customer email mailbox was accessed from the United States and from Russia less than an hour later, triggering an Impossible Travel Alert. Minutes later, an additional Alert was triggered by the creation and use of Anonymous Links to that Customer’s Microsoft OneDrive files. Early detection allowed for action to be taken to remove unauthorized access and limit data breach exposure.
Detection Details
AIS Managed SIEM combined and enriched log data as follows in this case:
- Added Geolocation, Country, and City Names to the IP Addresses provided by Office 365 Activity Access Logs.
- Identified an anomaly in the pattern of IP Address Country Names used by a particular Office 365 Account.
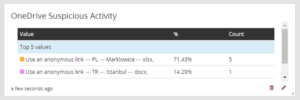
- Combined Office 365 Exchange Online audit logs with Microsoft OneDrive logs to identify additional threats.
The Alerts included links to AIS Managed SIEM dashboard for real-time threat status and detail.
Impossible travel activity:
Public-sharing links accessed from Poland and Turkey:
Early Detection Benefits:
- Unauthorized access to User mailbox removed quickly, limiting data breach exposure.
- Unexpected public-sharing links to private OneDrive files were removed that otherwise may not have been detected, limiting exposure to further data loss after unauthorized access had been removed.
More information about AIS Managed SIEM